During the last few years we have seen something quite unique happening – more and more people keep truly valuable information on their mobile devices: not only photos and videos of their loved ones, but also their emails, passwords and even credit card information. Needless to say, this has caught the attention of people with less-than-honorable intentions. As a whole, there are two types of attacks everyone should keep in mind – malware and in-person. Malware is distributed through apps, so thanks to the App Store policies and review process, this type of threat is virtually non-existent on iOS. The other type of threat – someone having physical access to your device – is just as serious and much more likely. So here are ten things you can do to make your iPhone or iPad as secure as possible against both types of threats.
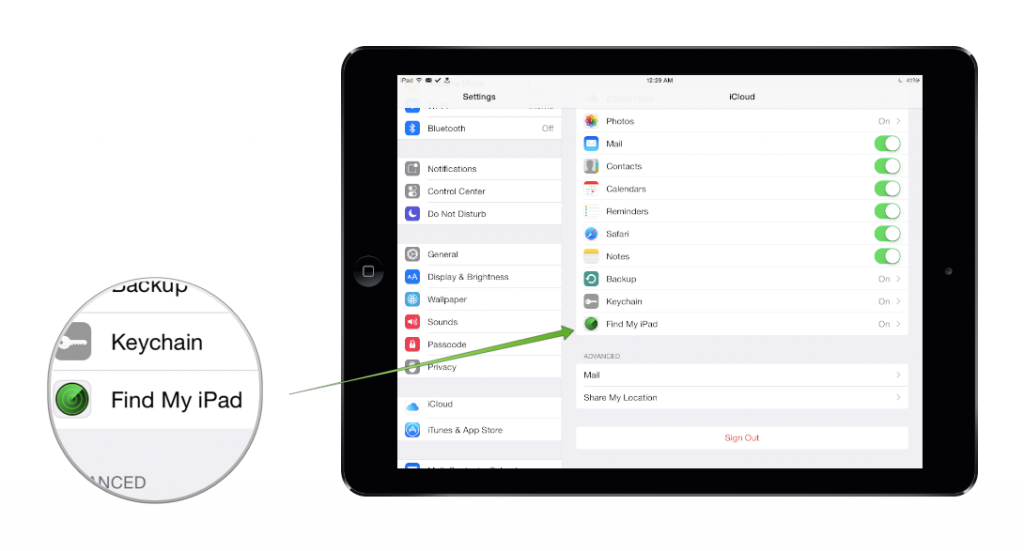
- Use Activation Lock.
Introduced in iOS 7, Activation Lock is the ultimate theft deterrent. As soon as you sign in with your Apple ID and turn on Find My iPhone by going to Settings and opening the iCloud section, your device will be locked to your Apple ID. This means that even if someone steals your phone or tablet and wipes it, they won’t be able to use it since your Apple ID and password are required for the device’s activation.
- Use a Passcode or TouchID.
This is perhaps the best way to ensure the safety of your data. To set a passcode to go Settings followed by Passcode.
If your device has a fingerprint sensor, opt for a strong password by disabling Simple Passcode. Since you’ll be unlocking your phone or tablet with your fingerprint, you’ll only need to enter the complex password after restarting the device.
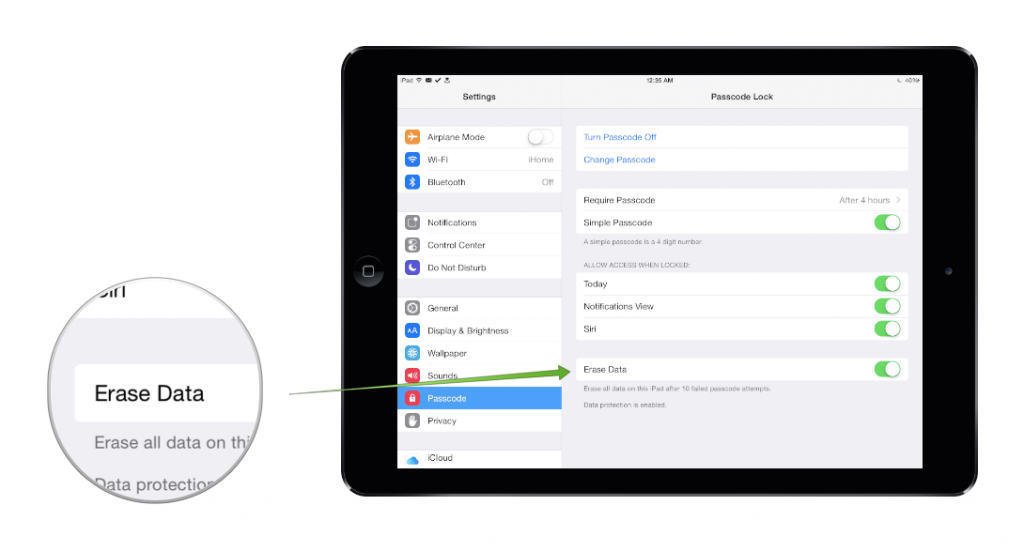
If you have sensitive information stored on your device and you use a numeric PIN as your passcode, we recommend turning on the Erase Data option. This will wipe your device after 10 failed attempts to enter the correct passcode. It is a good protective measure since numeric passcodes are theoretically easier to guess and easier to spot by another person in your vicinity. There are two things to keep in mind if you enable this option:
Back up regularly to iCloud or iTunes – there’s no guessing when you’ll find yourself with a wiped device.
Keep away from curious toddlers – kids love to explore anything and everything – including your easily-erased phone or tablet.
If you want maximum protection, you should also set Require Passcode to Immediately. On TouchID-enabled devices, you won’t notice a difference, but if you’re entering PIN numbers, you’ll have to enter the passcode every time you wake your iPhone or iPad.
The last passcode recommendation is to set the Auto-Lock to 1 or 2 Minutes.You can access this option by going to Settings and then tapping on General and Auto-Lock. This security measure will be most helpful to people who leave their iPhone or iPad unlocked and unattended for long periods of time. It will also help you save battery life.
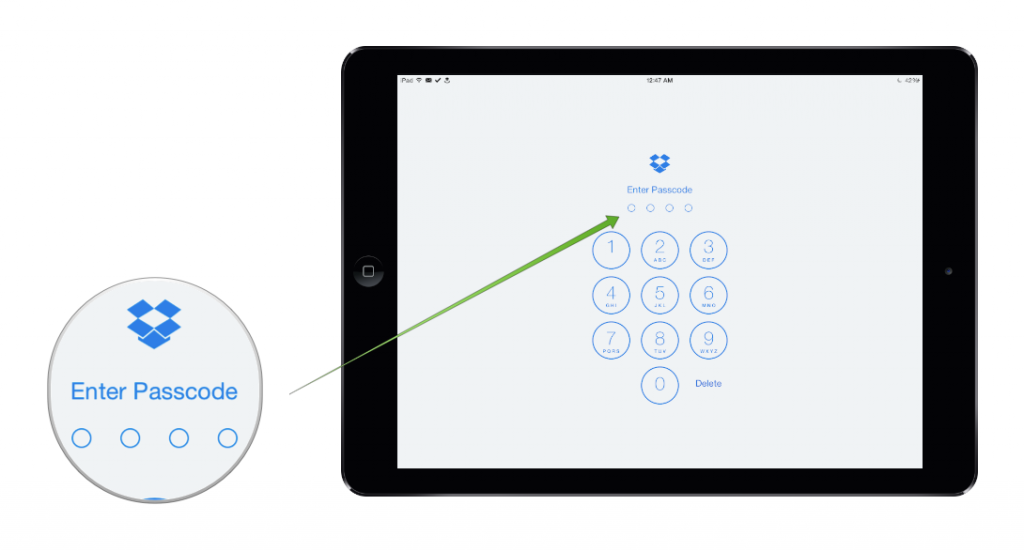
- Enable in-app Passcodes.
Many App Store developers have implemented their own security measures for their apps, the most common being a four-digit PIN code. We recommend taking advantage of this feature and using a PIN number that is different than your iOS passcode.
Tip: If you’re jailbroken, we recommend installing an app like iAppLock which can add an additional PIN code authentication to any app on your device.
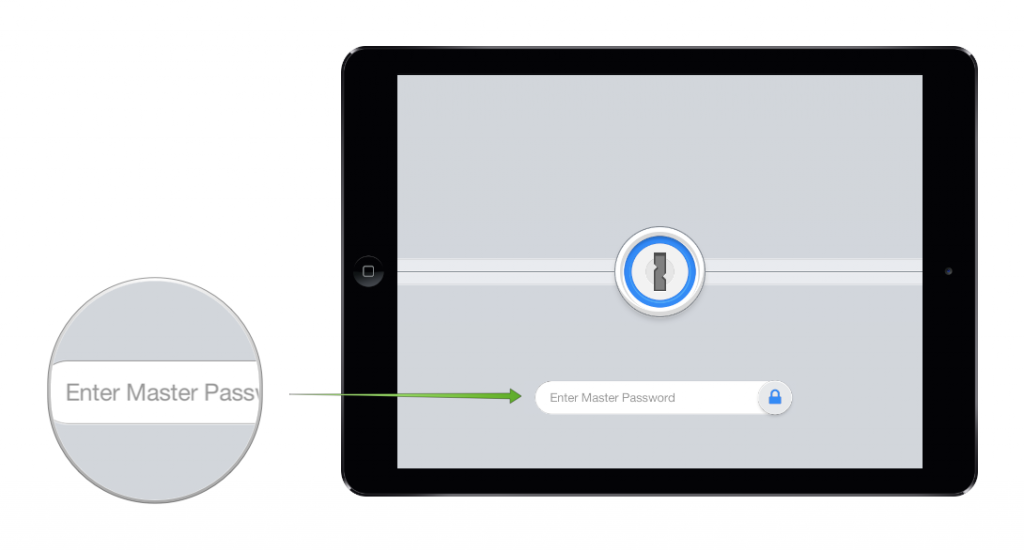
- Use a Password Manager.
Keeping with our theme of passcodes, we also recommend using a password manager like 1Password or iCloud Keychain to generate unique password for each site, app or service that you use.
There is a four-fold advantage to using a password manager:
Your passwords are much harder to guess – many brute force attacks at passwords use dictionaries and simply try every variation of all the words in the dictionary to try to guess your password. By using a random-character password, you render this attack totally ineffective.
One password to rule them all – when using a password manager, you’ll only be required to enter a singular master password of your choosing in order to unlock the array of random passwords for specific sites.
Your passwords can be very long – since you won’t be remembering each and every one, you can make your passwords insanely long. I personally use 30-character random passwords that are next to impossible to crack using present-day technology.
A single compromised site will not jeopardize you – we often read about major services being hacked and their users’ emails and passwords stolen. While having your login credentials for the site stolen is bad enough, most people use the same email-password combo to log in most of the services they use – including social media and potentially banking and other payment sites like PayPal. By using unique passwords every time, you compartmentalize your registrations, so a breach in security on one site will not endanger your other logins.

- Don’t jailbreak.
While being jailbroken does allow you a far greater level of control over your device, it requires quite a bit of security knowledge since it also exposes you to numerous attacks. Currently nearly all iOS malware can only affect jailbroken devices. In addition to malware, you also risk exposing your root filesystem to anyone on the same Wifi network as long as you don’t change your root password. Another drawback is the fact that being jailbroken locks you into a singular iOS version for a long time, so you’ll miss out on any bug fixes or security updates that may come out.
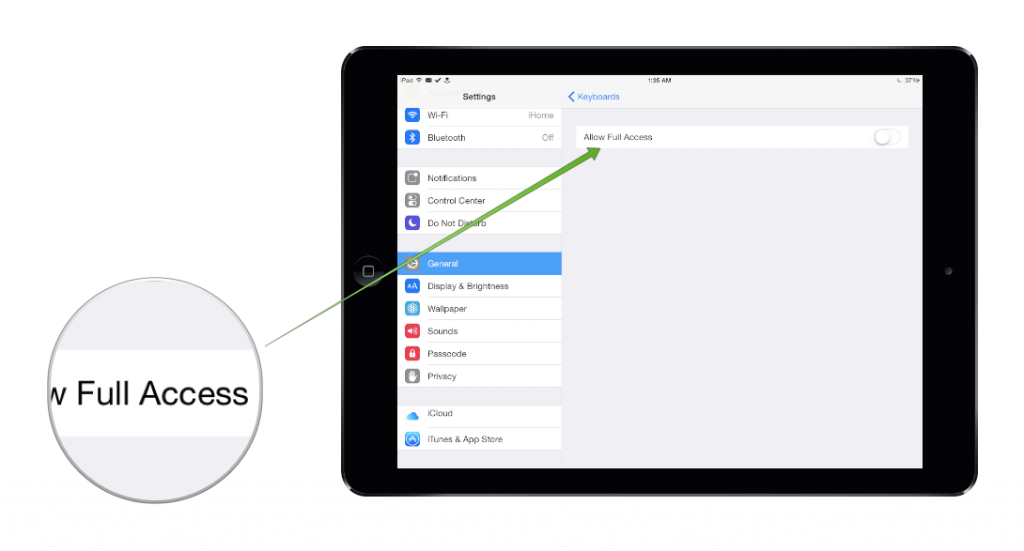
- Don’t give 3rd party keyboards Full Access unless you trust them entirely.
With iOS 8 we saw the debut of 3rd party keyboards like SwiftKey and Swype on the iPhone. And while being able to type by swiping is cool, is also poses a security risk, especially if the keyboard is more advanced. If you’re using a sophisticated keyboard, the developer might want you to grant the keyboard Full Access, which means that the keyboard can track what you type with it and communicate freely with the developer’s servers. While most developers would use this capability to sync your custom word dictionaries across your devices and use your data to improve their text prediction, some developers might have others, more sinister, plans in their minds. To revoke or grant Full Access to a 3rd party keyboard, go to Settings and tap on General, followed by Keyboard and Keyboards. Here tap on the 3rd party keyboard you’d like to inspect and choose whether to grant it Full Access by toggling Allow Full Access.
All in all, your safest bet is to either stick with the Apple keyboard or to use a 3rd party one with Full Access being permanently disabled.
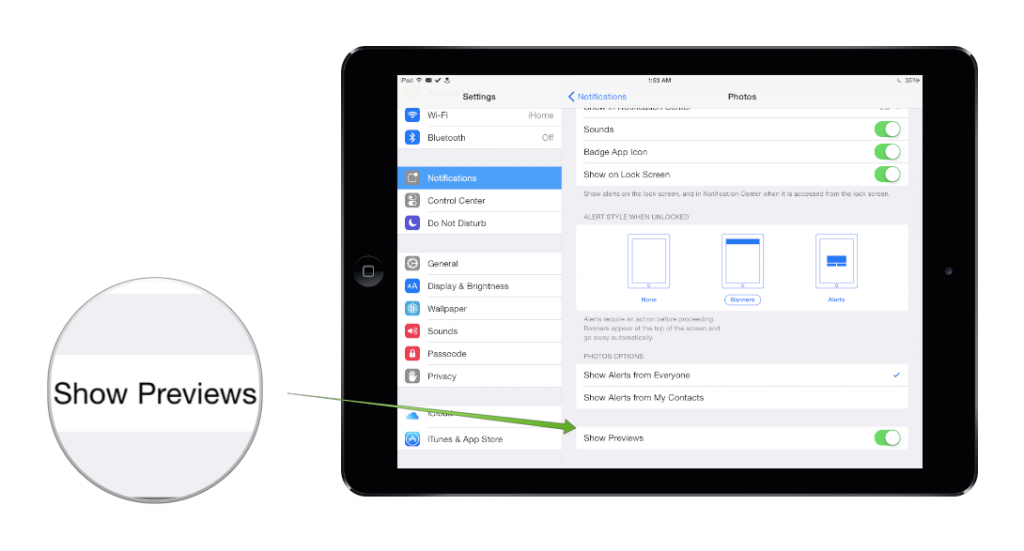
- Disable previews for messages, emails and photos.
Some types of notifications, such as messages, emails and shared photos, allow for a preview of the contents to be displayed on the lock screen when the notification is received. You can enhance your privacy by disabling this feature. To do so, open the Settings app and go to Notifications. There, tap on either Mail, Messages or Photos and turn off Show Previews.
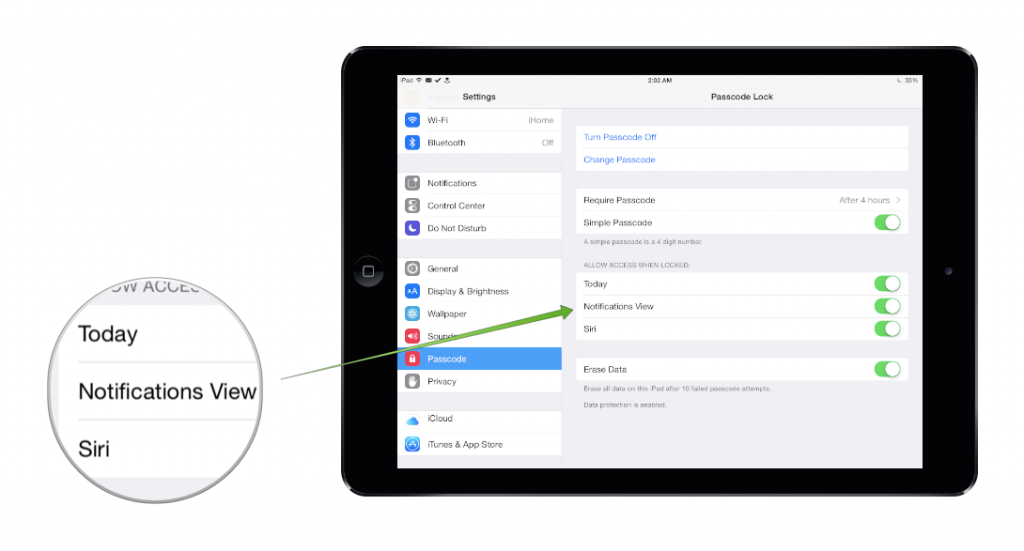
- Disable Siri, Control Center and Notification Center from the lock screen.
To disable those features, go to Settings and open Passcode. Here you can turn off Siri, the Today view and the Notifications View of Notification Center. To disable Control Center, go to Settings and choose Control Center. From there you can turn off Access on Lock Screen.
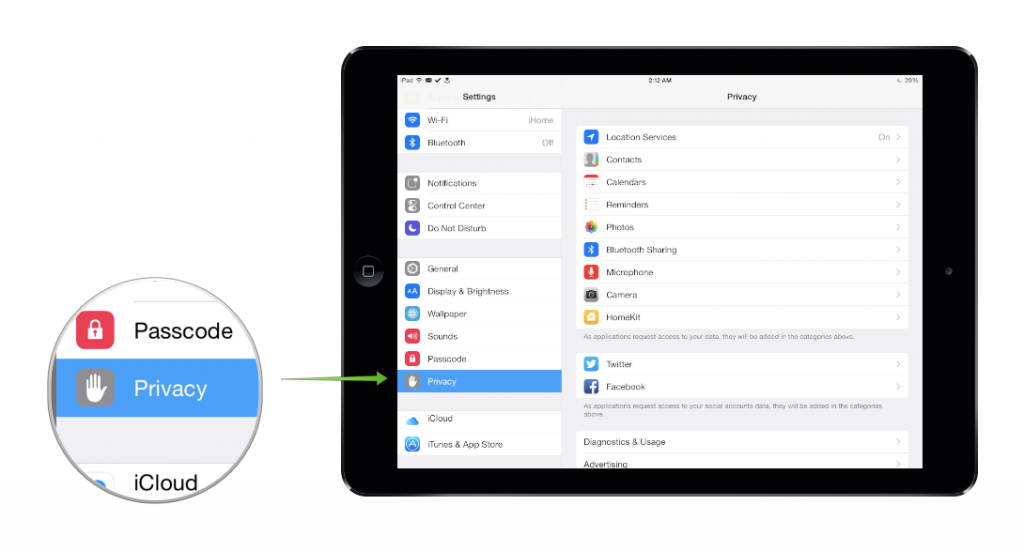
- Review the Privacy section in Settings.
This is a more general tip that should become a habit for the privacy- and security-conscious. By going to Settings and then Privacy, you can review all the access you’ve given to all App Store apps. If an app is given more access than you feel comfortable, feel free to change it. Keep in mind, however, that a large number apps require a certain level of access to function as advertised. If all access is denied, some apps will be crippled while other may be completely non-functioning.
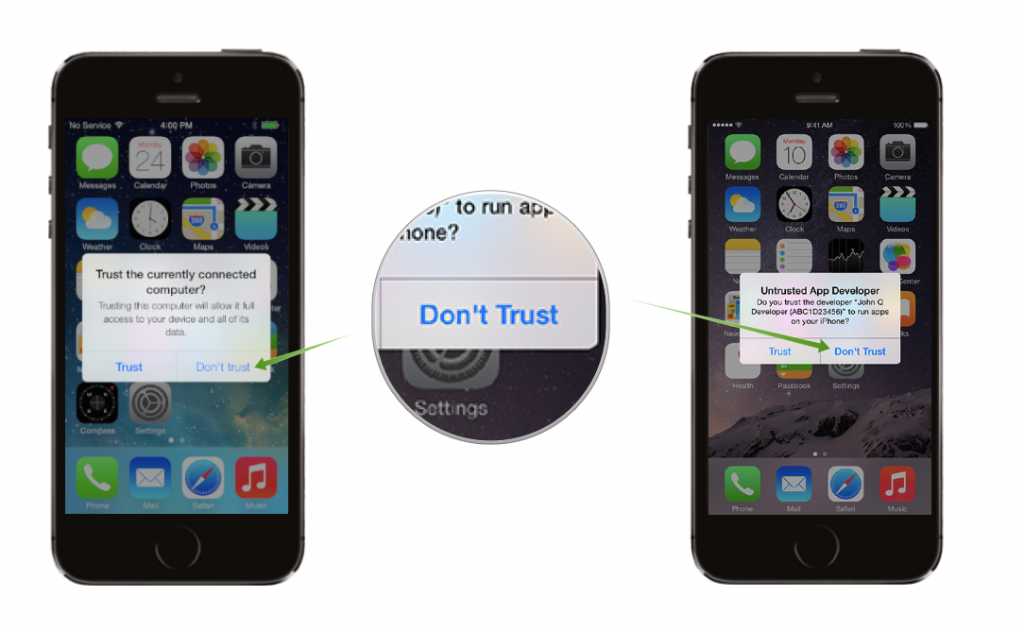
- Don’t Trust Untrusted Developers and connected computers.
Let’s tackle these two separately:
Don’t trust connected computers – unless the connected PC or Mac is your own machine, is it not a good idea to trust it since the option cannot be easily reversed. Once you choose to trust a computer, this computer will be able to automatically read the contents of your phone or tablet whenever it connects. So if another person gets a hold of your phone and the computer in question, they could potentially have access to the mobile device’s data.
Don’t trust Untrusted Developers – this one involves a highly unlikely scenario where a person with malicious intents will try to manipulate you into installing an app that mimics the look and feel of an original popular title from the App Store. Upon successful installation, the app will have access to the cache of the original app and it may also try to trick you into entering your credentials and then sending them over the web to the developer. This is potentially dangerous since the mimicked app can be your banking app or another one where you keep sensitive information.
This scam is achieved by using Apple’s enterprise solution for distributing apps outside of the App Store. You should not attempt to install any app outside the App Store and you should definitely not press the “Trust” button in the Untrusted App Developer dialog unless you know exactly what you’re doing and why.



